Your team discovers a critical vulnerability in your production systems. You check the CVE database and find nothing. You search vendor advisories and still come up empty. Three weeks later, you learn that researchers disclosed this vulnerability months ago through a GitHub advisory that never received a CVE number.
This situation happens more often than most security professionals realize. The traditional CVE system, while foundational, captures only a fraction of the vulnerability intelligence that modern security teams need.
Understanding the CVE Foundation
The Common Vulnerabilities and Exposures (CVE) system serves as the backbone of vulnerability tracking. MITRE Corporation maintains this database, assigning unique identifiers to each vulnerability. Think of CVE numbers as social security numbers for security flaws - they create a universal reference system that allows different tools and teams to discuss the same vulnerability.
CVE entries contain basic information: a unique identifier, a brief description, and references to additional sources. However, CVE entries lack crucial details that security teams need for risk assessment. They don't include severity scores, exploitation difficulty, or remediation guidance.
This limitation leads us to the next layer of vulnerability intelligence.
The National Vulnerability Database: Adding Context
The National Institute of Standards and Technology (NIST) operates the National Vulnerability Database (NVD), which takes CVE entries and enriches them with actionable data. The NVD adds Common Vulnerability Scoring System (CVSS) scores, attack vector analysis, and impact assessments.
CVSS scores help security teams prioritize their response efforts. A vulnerability with a CVSS score of 9.8 demands immediate attention, while a score of 3.1 might wait for the next maintenance window. The NVD also provides information about attack complexity, required privileges, and potential impact on confidentiality, integrity, and availability.
However, even this enhanced information has gaps. The CVE assignment process can take weeks or months, creating dangerous windows where vulnerabilities exist but lack official documentation.
Commercial Intelligence Sources
Several commercial databases fill these gaps by tracking vulnerabilities that never receive CVE numbers. Risk Based Security's VulnDB contains over 200,000 vulnerabilities compared to roughly 180,000 in the CVE database. This difference represents thousands of security flaws that traditional CVE tracking misses.
VulnDB focuses on speed and completeness. They track vulnerabilities in products that CVE traditionally ignores, such as mobile applications, web applications, and specialized industrial systems. They also provide faster notification than official channels, sometimes beating CVE assignments by weeks.
Offensive Security maintains the Exploit Database, which serves a different purpose. While CVE tells you a vulnerability exists, the Exploit Database shows you exactly how attackers use it. This database contains proof-of-concept code and detailed exploitation techniques that help security teams understand real-world risk.
Open Source and Vendor-Specific Sources
GitHub Security Advisories represent a growing trend in vulnerability disclosure. Open source projects publish advisories directly on GitHub when they discover security issues. This creates faster disclosure cycles but also fragments the information across thousands of individual repositories.
Google's Open Source Vulnerabilities (OSV) database attempts to solve this fragmentation. OSV aggregates vulnerability information from multiple open source ecosystems and maps vulnerabilities to specific code commits rather than just version numbers. This precision helps developers understand exactly which code changes introduce or fix security issues.
Major software vendors maintain their own security advisories that often contain information not found anywhere else. Microsoft Security Response Center, Adobe Security Bulletins, and Oracle Critical Patch Updates provide vendor-specific details about vulnerabilities, workarounds, and remediation steps.
Emerging Trends Reshaping Vulnerability Intelligence
The vulnerability intelligence field is changing rapidly, driven by automation, artificial intelligence, and new attack patterns. Understanding these trends helps security professionals prepare for future challenges.
Automated vulnerability discovery tools now scan code repositories continuously, finding security flaws faster than human researchers can process them. This automation creates both opportunities and challenges. Teams get earlier warning about potential vulnerabilities, but they also face information overload from false positives and low-priority findings.
Supply chain attacks like SolarWinds have shifted focus toward dependency tracking. Modern applications use hundreds of third-party libraries, each with their own vulnerability profiles. Traditional CVE tracking struggles with this complexity because vulnerabilities in dependencies affect multiple downstream applications.
Machine learning systems now predict where vulnerabilities might exist before researchers discover them. These systems analyze code patterns, commit histories, and developer behavior to identify high-risk areas. While promising, this approach generates thousands of predictions that require human verification.
The Risk Scoring Evolution
CVSS scores, while useful, often fail to reflect real-world risk. A vulnerability with a theoretical CVSS score of 9.0 might pose minimal risk if no exploitation tools exist and the affected system has limited exposure. Conversely, a vulnerability with a moderate CVSS score might demand immediate attention if active exploitation campaigns target it.
New scoring systems attempt to address these limitations by incorporating threat intelligence data. The Exploit Prediction Scoring System (EPSS) estimates the likelihood that a vulnerability will be exploited in the wild within the next 30 days. This probabilistic approach helps security teams focus on vulnerabilities that attackers actually use rather than those with theoretical high scores.
Stakeholder-Specific Vulnerability Categorization (SSVC) takes a different approach by asking decision-making questions: How exploitable is this vulnerability? What is the utility to an attacker? How exposed are our systems? This framework helps organizations make risk-based decisions rather than relying solely on numerical scores.
Building Your Intelligence Strategy
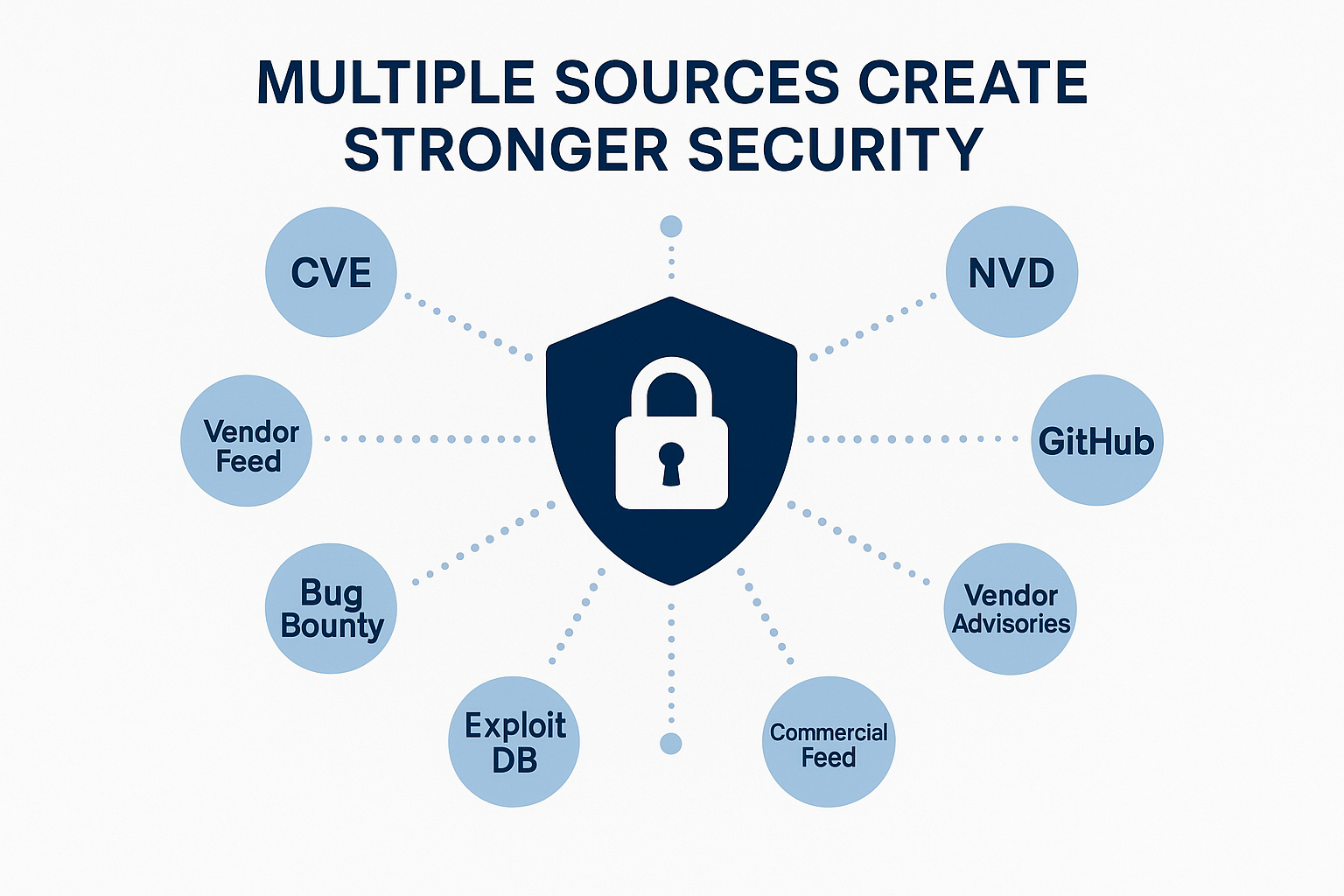
Effective vulnerability intelligence requires multiple data sources working together. No single database provides complete coverage of the modern threat environment. Security teams need strategies that combine traditional CVE data with commercial intelligence, vendor advisories, and threat intelligence feeds.
Start by mapping your technology stack to relevant data sources. If you use primarily commercial software, focus on vendor advisories and traditional CVE sources. If you rely heavily on open source components, prioritize GitHub Security Advisories and OSV data. Cloud-native environments require different sources than traditional on-premises infrastructure.
Automation becomes crucial as you expand your data sources. Manual correlation of vulnerability data across multiple databases quickly becomes impossible at scale. Security orchestration platforms can aggregate data from multiple sources, deduplicate findings, and present unified risk assessments.
Integration Challenges and Solutions
The biggest challenge in modern vulnerability intelligence is integration. Different databases use different formats, update schedules, and identification schemes. A single vulnerability might have a CVE number, a GitHub advisory identifier, a vendor-specific bulletin number, and multiple commercial database entries.
APIs help solve integration challenges by providing standardized access to vulnerability data. The CVE Program recently introduced CVE Services, which provides programmatic access to CVE data. GitHub offers APIs for security advisories, and most commercial vendors provide similar interfaces.
Security teams should prioritize tools that support multiple data formats and can correlate vulnerabilities across different identification schemes. This correlation capability becomes essential as vulnerability intelligence becomes more distributed across specialized databases.
The Human Element
Despite increasing automation, human expertise remains crucial in vulnerability intelligence. Automated systems excel at data collection and basic correlation, but they struggle with context and nuance. Security professionals must interpret threat intelligence, assess business impact, and make risk-based decisions that no algorithm can automate.
Successful vulnerability intelligence programs combine automated data collection with human analysis. Machines handle the heavy lifting of data aggregation and initial filtering while humans focus on strategic decision-making and complex risk assessment.
Practical Next Steps
Security professionals should audit their current vulnerability intelligence sources and identify gaps. Many teams rely exclusively on traditional CVE sources and miss significant portions of the vulnerability universe. Start by mapping your technology stack to relevant databases and establishing regular monitoring processes.
Consider implementing a threat intelligence platform that can aggregate data from multiple sources and provide unified risk assessment. These platforms reduce the manual effort required to monitor dozens of different databases and advisories.
Establish relationships with security researchers and vendor security teams. These connections often provide early warning about emerging vulnerabilities before they appear in public databases. The security community remains surprisingly collaborative, and many researchers share information through informal channels.
The vulnerability intelligence field will continue evolving as new threats emerge and attack patterns change. Security professionals who understand multiple data sources and can adapt their strategies accordingly will be better positioned to protect their organizations in an increasingly complex threat environment.
The key insight here is that vulnerability intelligence has become a discipline that requires both technical skills and strategic thinking. The days of simply monitoring CVE feeds are over. Modern security teams need comprehensive intelligence strategies that combine multiple data sources, automated tools, and human expertise to stay ahead of evolving threats.
https://bit.ly/44mozPd
https://bit.ly/4lmtRQN
https://guptadeepak.com/content/images/2025/07/Building-a-Complete-CVE-systsem---guptadeepak.com.png
https://guptadeepak.weebly.com/deepak-gupta/beyond-cve-building-a-complete-vulnerability-intelligence-strategy


No comments:
Post a Comment