System for Cross-domain Identity Management (SCIM) is an open standard designed to simplify user identity management in cloud-based applications and services. This article provides a deep technical dive into SCIM, exploring its functionality, value in identity and access management (IAM), impact on Single Sign-On (SSO), and key concepts illustrated through charts and diagrams.
What is SCIM?
SCIM is a standardized API for managing user identities. It provides a defined schema for representing users and groups and a REST API for reading and writing identity data to cloud applications. The current version, SCIM 2.0, was approved by the IETF as RFC 7643 and RFC 7644 in 2015.
Key characteristics of SCIM include:
- RESTful protocol
- JSON-based data model
- Standardized schema for user and group objects
- Support for create, read, update, and delete (CRUD) operations
- Extensible to support custom attributes
How SCIM Works
SCIM operates on a client-server model:
- SCIM Client: Typically an identity provider (IdP) or an identity management system.
- SCIM Server: The application or service where user accounts must be managed.
The basic workflow is as follows:
- The SCIM client sends HTTP requests (GET, POST, PUT, PATCH, DELETE) to the SCIM server's endpoints.
- These requests contain user or group data in JSON format, conforming to the SCIM schema.
- The SCIM server processes these requests, performing the appropriate CRUD operations on its user database.
- The server sends back HTTP responses, often including the updated user or group data.
Key Components of SCIM
SCIM Schema
SCIM defines a core schema for user and group objects. The basic user object might look like this:
{ "schemas": ["urn:ietf:params:scim:schemas:core:2.0:User"], "id": "2819c223-7f76-453a-919d-413861904646", "userName": "jsmith@example.com", "name": { "formatted": "Mr. John Smith", "familyName": "Smith", "givenName": "John" }, "emails": [ { "value": "jsmith@example.com", "type": "work", "primary": true } ]}SCIM API Endpoints
SCIM defines several REST API endpoints:
/Usersfor user management/Groupsfor group management/Schemasfor retrieving the supported schemas/ResourceTypesfor discovering supported resource types/ServiceProviderConfigfor retrieving service provider configuration
SCIM Operations
SCIM supports standard CRUD operations:
- Create: POST request to create new resources
- Read: GET request to retrieve resources
- Update: PUT or PATCH request to modify existing resources
- Delete: DELETE request to remove resources
Value of SCIM in Identity and Access Management
SCIM provides several key benefits in IAM:
- Standardization: SCIM offers a standardized way to manage user identities across multiple systems, reducing the need for custom integrations.
- Automation: It enables automated user provisioning and de-provisioning, reducing manual effort and the potential for errors.
- Real-time Synchronization: SCIM allows for real-time updates to user information across connected systems.
- Scalability: As organizations add new applications, SCIM provides a consistent method for identity management.
- Improved Security: Automated de-provisioning helps ensure that access is promptly revoked when users leave an organization.
- Compliance: SCIM helps organizations maintain compliance with regulations by providing a consistent, auditable method for managing user access.
SCIM's Impact on Single Sign-On (SSO)
While SCIM and SSO are separate technologies, they complement each other in meaningful ways:
- User Provisioning for SSO: SCIM automates the creation of user accounts in target applications, ensuring that users have accounts to sign into when using SSO.
- Consistent User Attributes: SCIM ensures that user attributes are consistent across applications, which is crucial for attribute-based access control in SSO systems.
- Lifecycle Management: SCIM handles the full lifecycle of user accounts, including updates and deactivation, which SSO alone doesn't address.
- Enhanced Security: The combination of SCIM and SSO provides both convenient access (SSO) and proper access management (SCIM), enhancing overall security.
SCIM Architecture and Workflow
To simplify understanding of SCIM, let's visualize some key concepts:
SCIM Architecture
The SCIM architecture facilitates identity data exchange between identity providers (IdPs) and service providers (SPs). Let's break down the key components:
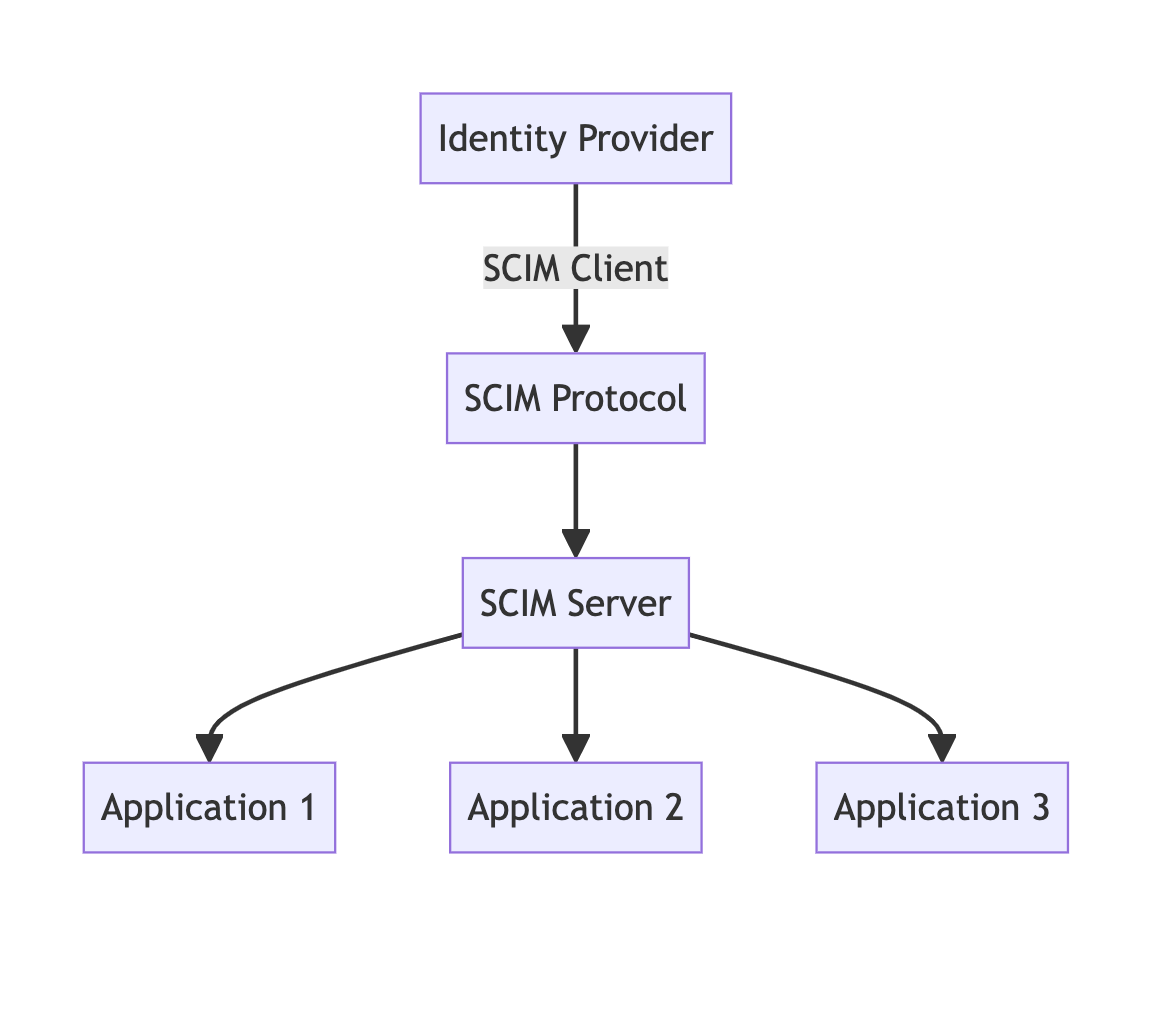
- SCIM Client (Identity Provider):
- Typically part of an IdP or identity management system.
- Initiates SCIM requests to manage user identities across multiple systems.
- Responsible for creating, reading, updating, and deleting user information.
- SCIM Protocol:
- Defines the RESTful API and data model for identity management operations.
- Uses HTTP methods (GET, POST, PUT, PATCH, DELETE) for CRUD operations.
- Employs JSON as the primary data format for request and response payloads.
- SCIM Server (Service Provider):
- Implemented by the application or service where user accounts need to be managed.
- Exposes SCIM endpoints to receive and process SCIM requests.
- Translates SCIM operations into application-specific actions on the user database.
4. Target Applications:
- The end systems where user accounts are actually created, updated, or deleted.
- May have their own user stores that are updated via the SCIM server.
This architecture allows for a standardized approach to identity management across diverse systems, reducing the need for custom integrations between each IdP and SP.
SCIM Workflow
The SCIM workflow encompasses various scenarios for identity management. Here is a typical workflow in detail:
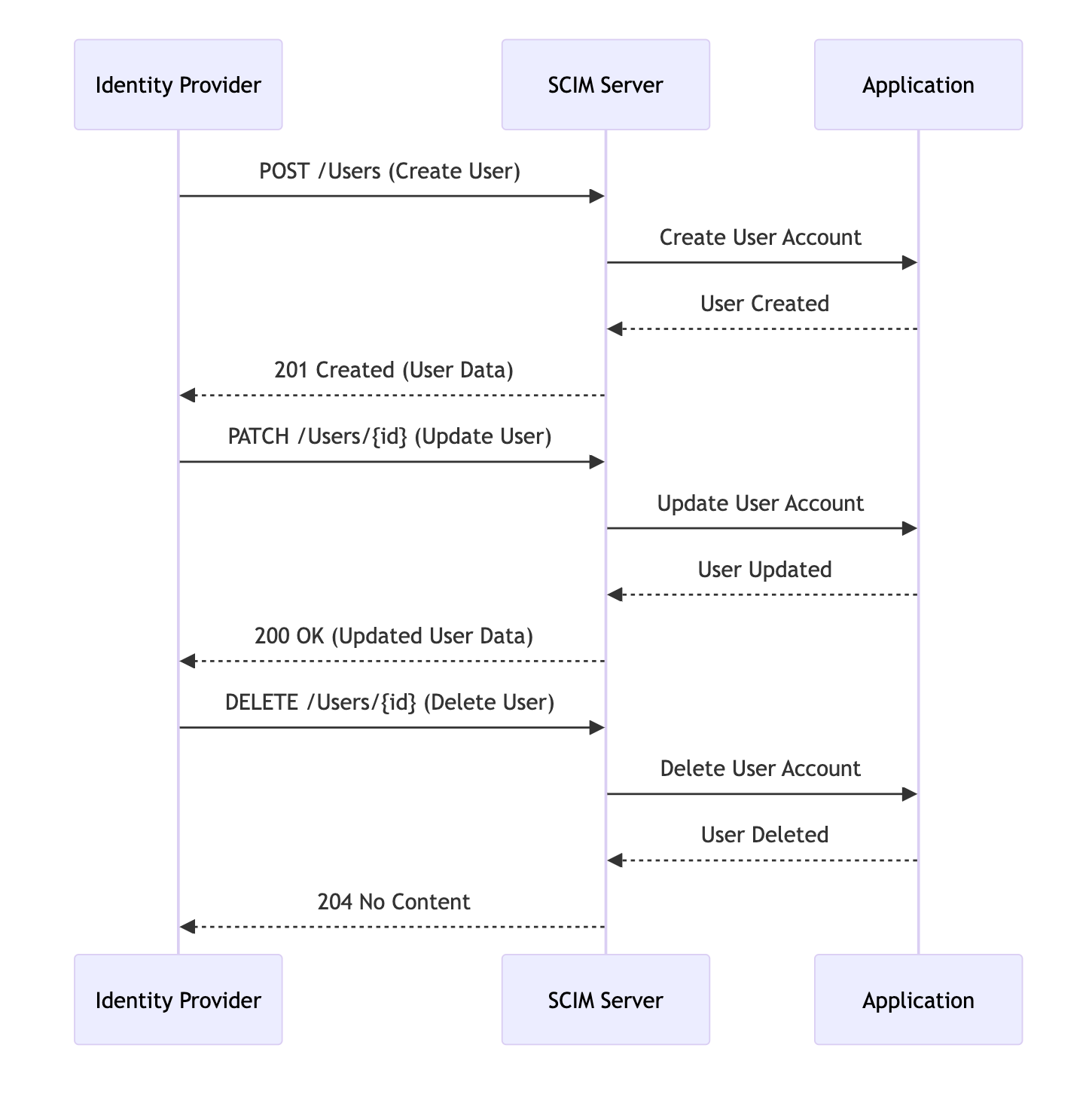
- User Provisioning:
- The SCIM client (IdP) sends a POST request to the
/Usersendpoint of the SCIM server. - The request payload contains the user's JSON information, adhering to the SCIM schema.
- The SCIM server validates the request and creates the user account in the target application.
- The server responds with a 201 Created status and the newly created user's details.
- User Attribute Update:
- The SCIM client sends a PATCH request to
/Users/{id}with the updated attributes. - The SCIM server processes the request and updates the user's information in the target application.
- The server responds with a 200 OK status and the updated user data.
- User Retrieval:
- The SCIM client sends a GET request to
/Users/{id}or/Userswith filter parameters. - The SCIM server retrieves the requested user information from the target application.
- The server responds with a 200 OK status and the requested user data.
- User Deprovisioning:
- The SCIM client sends a DELETE request to
/Users/{id}. - The SCIM server processes the request and removes or deactivates the user account in the target application.
- The server responds with a 204 No Content status, indicating successful deletion.
This workflow demonstrates how SCIM facilitates real-time, automated identity management across systems, ensuring consistency and reducing manual intervention.
SCIM and SSO Interaction
While SCIM and SSO are distinct technologies, they work together to provide a comprehensive identity management and authentication solution. Here's a detailed look at their interaction:
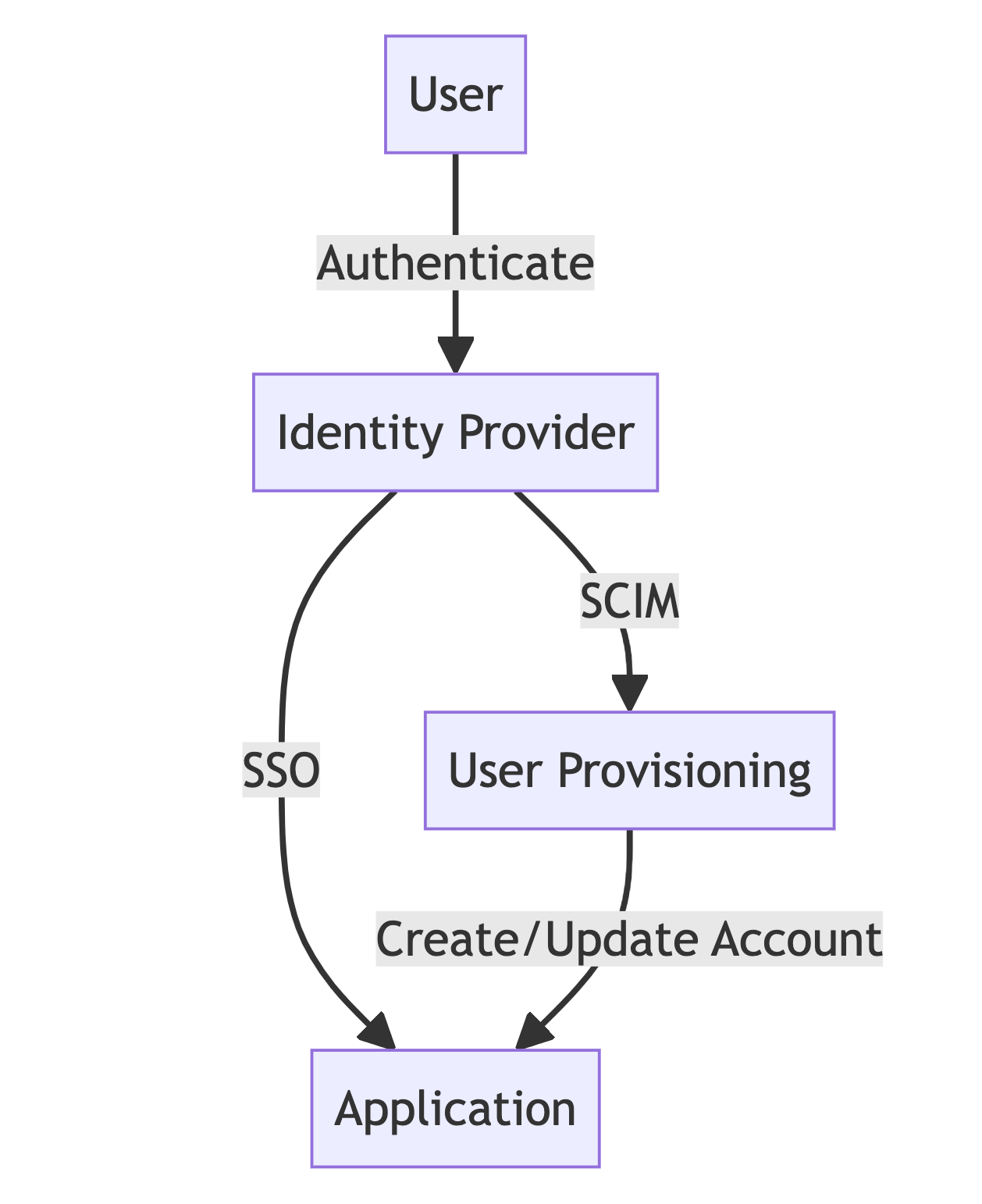
- User Provisioning for SSO:
- When a new user is added to the IdP, SCIM automatically provisions the user account in SSO-enabled applications.
- This ensures that their account already exists when the user attempts to access an application via SSO.
2. Attribute Synchronization:
- SCIM keeps user attributes consistent across all connected applications.
- When a user authenticates via SSO, the application can rely on these synchronized attributes for authorization decisions.
3. Just-in-Time (JIT) Provisioning:
- In some SSO flows, user accounts are created on-the-fly when a user first accesses an application.
- SCIM can be used to enhance this process by providing a richer set of user attributes during JIT provisioning.
4. Session Management:
- While SSO manages active user sessions, SCIM ensures that the underlying user accounts remain up-to-date.
- If a user's access rights change, SCIM updates this information across all applications, which can then be reflected in the user's SSO sessions.
5. Deprovisioning and Access Revocation:
- When a user leaves an organization, SCIM can automatically deprovision their accounts across all connected applications.
- This complements SSO by ensuring that not only is the user's session terminated, but their accounts are also properly deactivated or removed.
6. Multi-Factor Authentication (MFA) Support:
- SCIM can be used to synchronize MFA settings and credentials across applications.
- This allows for consistent application of MFA policies in conjunction with SSO authentication.
SCIM and SSO create a more secure, efficient, and user-friendly identity management ecosystem by working together. SCIM ensures that the proper accounts exist with the correct attributes, while SSO provides a seamless authentication experience for users.
Conclusion
SCIM plays a crucial role in modern identity and access management by providing a standardized, efficient method for managing user identities across multiple systems. Its ability to automate user provisioning and de-provisioning, coupled with its complementary relationship with SSO, makes it an essential component of a robust IAM strategy. As companies continue to adopt more cloud services, the importance of SCIM in maintaining consistent, secure, and manageable user identities will only grow.
https://bit.ly/4bKgjZP
https://bit.ly/4fbGqLW
https://guptadeepak.com/content/images/2024/07/SCIM-secure-cloud-applications-1.webp
https://guptadeepak.weebly.com/deepak-gupta/securing-cloud-applications-scims-role-in-modern-identity-management


No comments:
Post a Comment